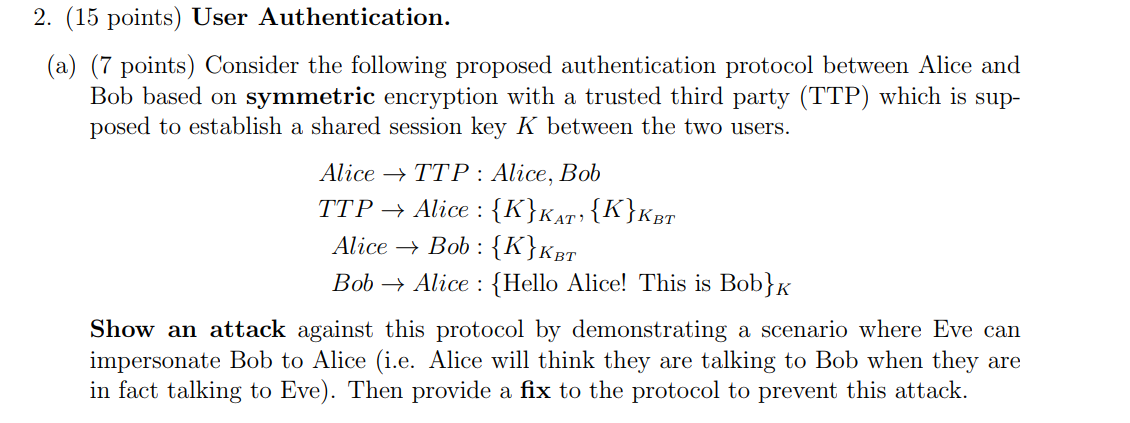
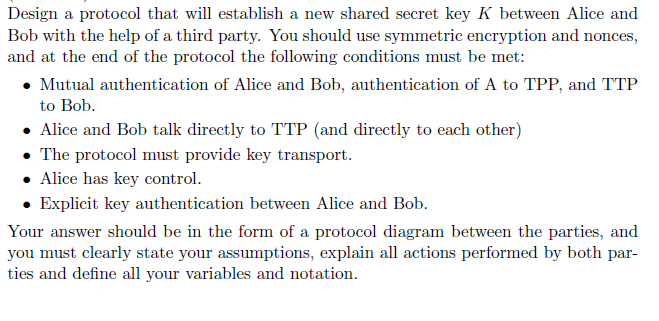
How Does Trent Send a Cipher Message to Bob, Alice and Carol, And Not Know What Reads the Message? | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

PPT – Biological Weapons of Mass Destruction PowerPoint presentation | free to view - id: 1b525-MDk1M
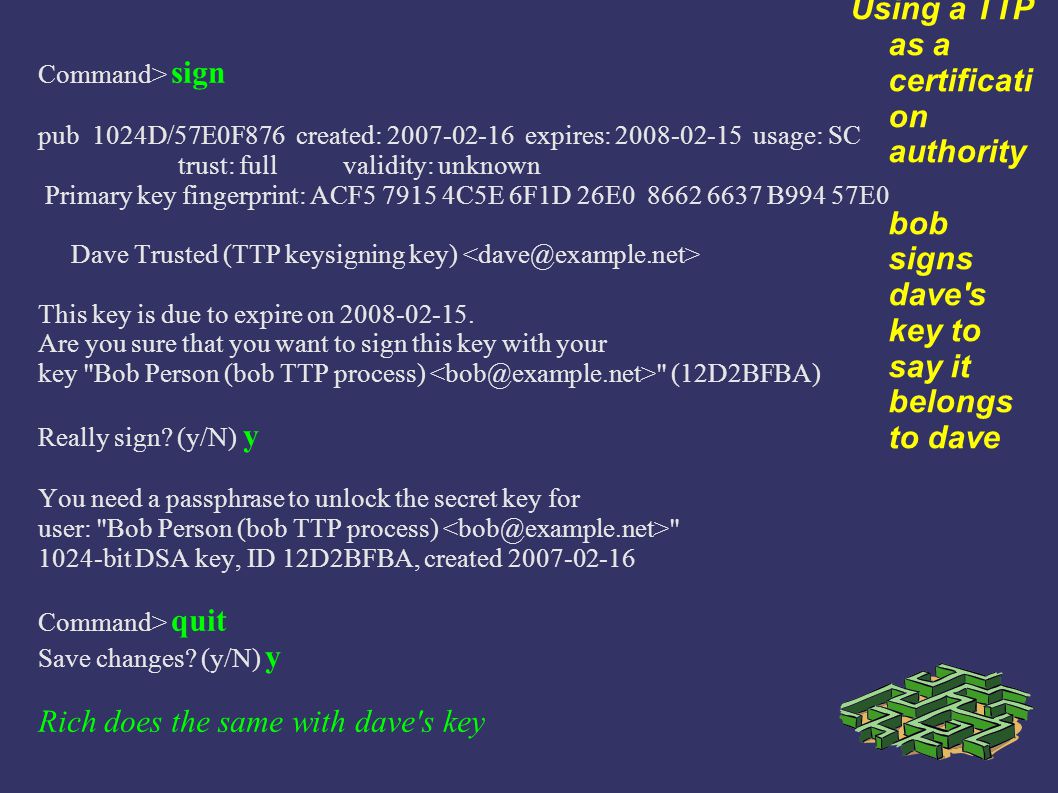
Using GPG - the GNU Privacy Guard Why does a security professional need this skill ? 3 GPG HOWTO's Use by checking Correspondents' Keys Directly Using. - ppt download

Using GPG - the GNU Privacy Guard Why does a security professional need this skill ? 3 GPG HOWTO's Use by checking Correspondents' Keys Directly Using. - ppt download